Trend Agentic AI SIEM
The Trend Agentic AI SIEM agent is another example of a company rushing out an AI function without proper design considerations. Rather than focusing on some tedious time consuming tasks AI is better suited for such as log parsing, instead it is focused on trying to replace the thinking of a SOC analyst.
When writing a OSQuery in the Trend Vision One console it surfaced a shiny “use AI” button to assist me so I thought I would give it a go. I clicked on it and entered my query and pressed submit, then waited….and waited…..then while waiting I decided to open another tab and ask google the same question which it promptly returned the correct answer/syntax in the top article. Switching back to the VisionOne console I continued to wait….and then eventually a reply came. I copied and pasted it in and pressed enter only to have VisionOne tell me the OSQuery that its own AI returned was incorrect.
Sadly instead of shoving a “use AI” button down my throat, Trend would have been better suited to have a “Click to use google” button. I’m not sure who is doing the QA for the features at Trend but they need to do a better job.
Microsoft Sentinel Security CoPilot
SentinelOne Purple AI
Purple AI supports a variety of data sources to enhance threat detection and investigation capabilities. The following are the key data sources that Purple AI can work with:
-
Native Data Sources: These are the built-in data sources that come with SentinelOne’s platform.
-
Third-Party Log Sources: Purple AI has expanded its support to include several widely used third-party log sources, which are:
- Palo Alto Networks Firewall
- ZScaler Internet Access
- Proofpoint TAP
- Microsoft Office 365
- Fortinet FortiGate
- Okta
Ok, awesome! so Purple AI supports Microsoft Office 365 data source which we were ingesting. Lets ask it a basic question about a users O365 activity and it returns the below.
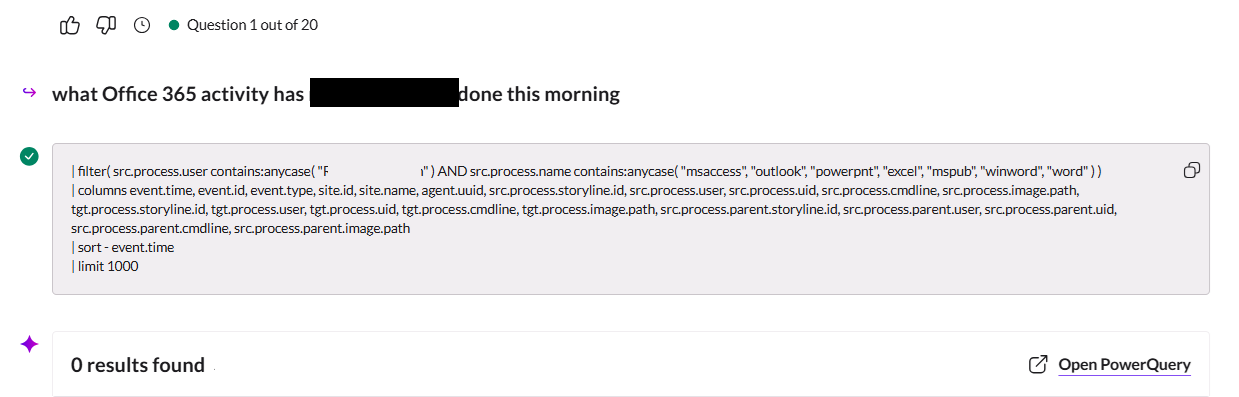
Its formatted a query for a data source we don’t have, its certainly not the Office 365 data source as the username isn’t in the correct format. It is most likely formatted for data ingested by the SentinelOne EDR agent (which we dont have).
I stil don’t think I have managed to return a sensible answer from purple AI yet, maybe its because I’m not entering the prompts right but its at the point where a user is better off learning the event search syntax and writing the queries themself. The biggest issue still seems to be the SentinelOne EDR agent tie ins. You can work around them but it would be much better if the vendor properly decoupled the EDR agent from Purple AI SIEM