Posted inAI sentinel SentinelOne
A long way to go for AI implementations in SIEM platforms
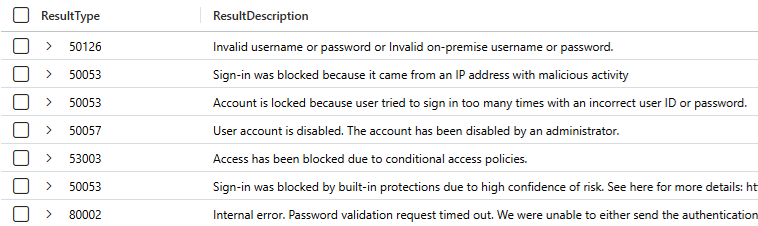
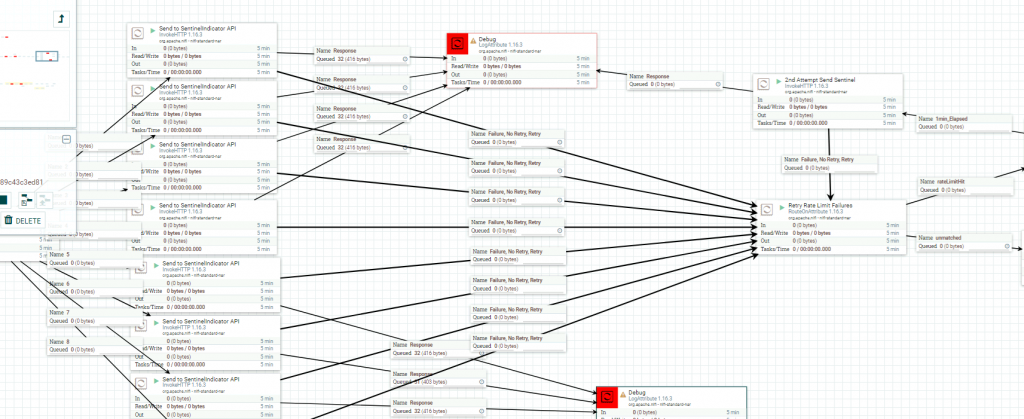
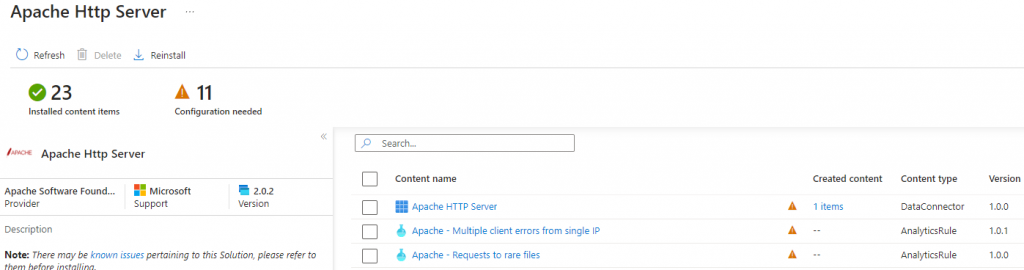
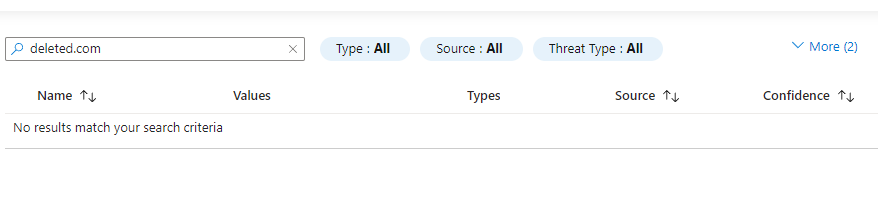
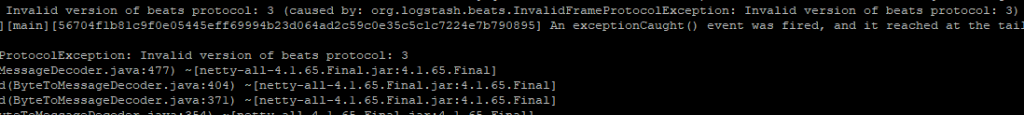
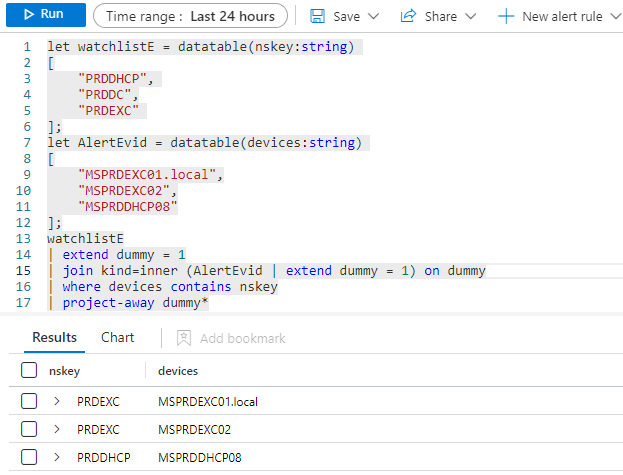
Trend Agentic AI SIEM The Trend Agentic AI SIEM agent is another example of a company rushing out an AI function without proper design considerations. Rather than focusing on some…