Manage My Health Breach
A long way to go for AI implementations in SIEM platforms
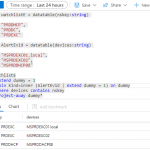
Nifi Groovyscript to convert JSON table array to key value JSON format
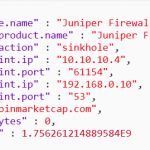
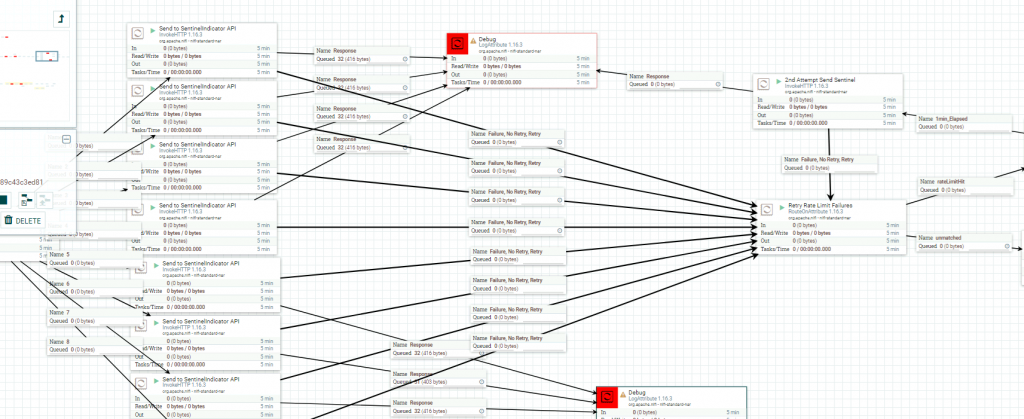
SentinelOne AI SIEM Indicator API
Threat Intelligence in SentinelOne AI Siem
Endpoint URL: https://{your sentinelone console domain}/web/api/v2.1/threat-intelligence/iocs
Headers Required: Authorization Content-Type
Official Documentation: https://{your sentinelone console domain}/new-api-docs
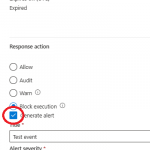
Limitations of the SentinelOne AI SIEM Threat Intelligence API:
- It can take up to 25 minutes for a new IoC to become active.
- The database can hold up to 1 million IoC entries per scope and an error shows after the limit is reached.
- The DELETE command does not filter by method, pattern, or patternType.
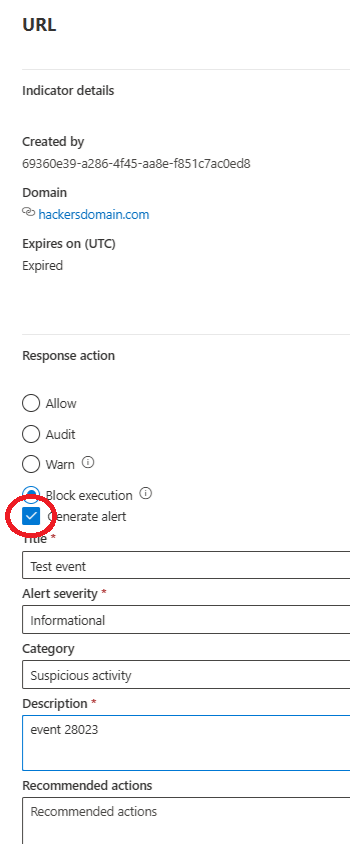
These values under data are required fields: "source", "type", "value", and "method".
"Type" and "method" must be in upper case.
The “validUntil” field is mandatory, and must contain a date, for example, 2021-03-20 09:14:47.779000. “validUntil” determines when the IOC expires.
If the expiration date (“validUntil”) is left blank, by default it will be the upload date plus a default offset value:
- 14 days for IPs
- 90 days for URLs and domains
- 180 days for file hashes (SHA1, SHA256, and MD5)
The maximum offset values allowed are:
- 30 days for IPs
- 180 days for URLs and Domains
- 180 days for hashes (SHA1, SHA256, and MD5)
IOC types it can handle are (uppercase) SHA1, SHA256, MD5, IPV4, IPV6, DNS, URL
The upload date is when the API gets a request to create an IOC.
If the expiration date is later than the upload date plus the the maximum offset value allowed, it will be adjusted to the upload date plus the maximum offset value allowed.